Court finds NSO Group liable for hacking WhatsApp users in landmark spyware ruling
Federal judge rules NSO Group violated computer fraud laws by deploying Pegasus spyware through WhatsApp's servers in California.
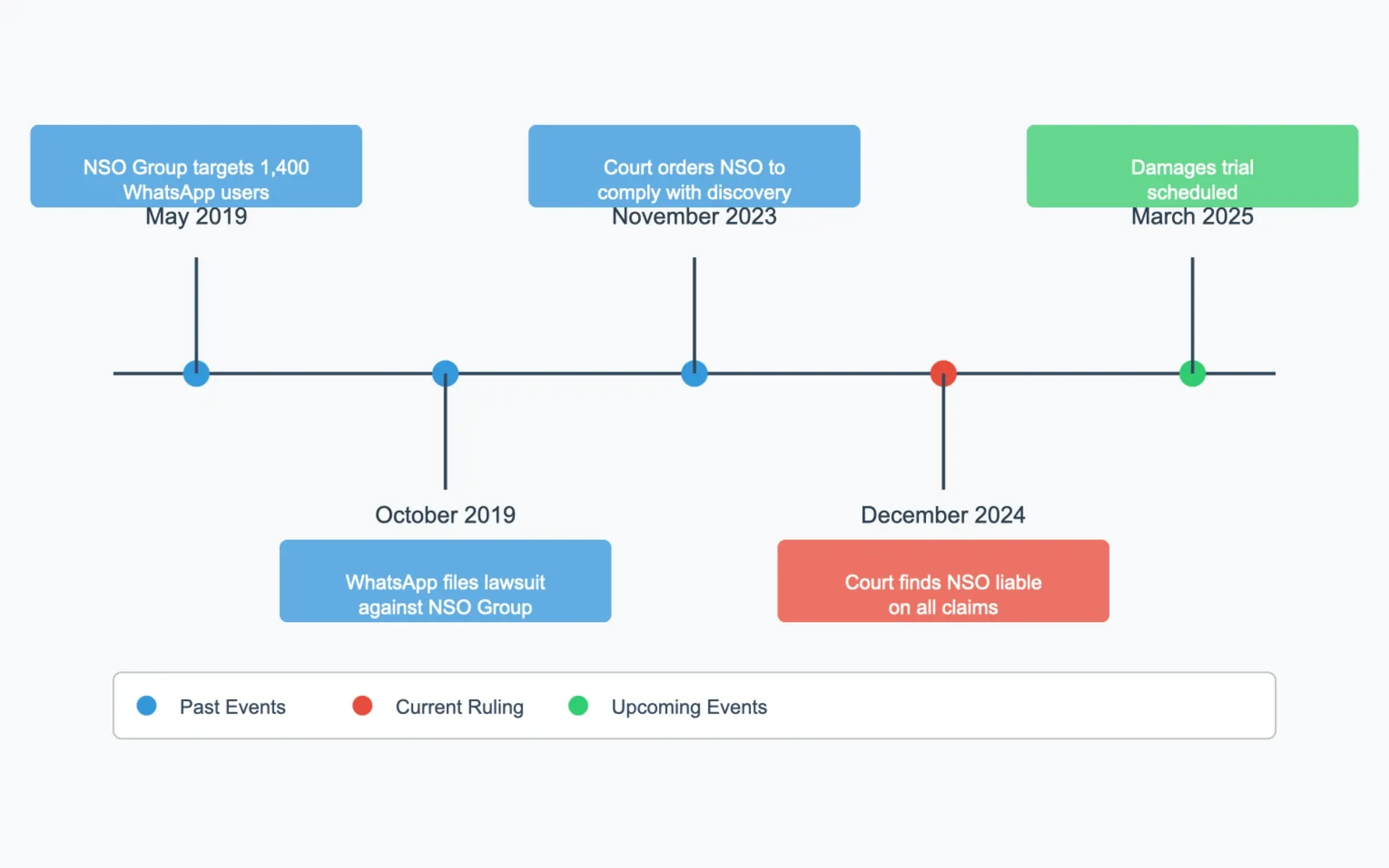
Just one day ago, on December 20, 2024, the United States District Court for the Northern District of California handed down a significant ruling against NSO Group, finding the Israeli spyware company liable for hacking WhatsApp users through its Pegasus surveillance software.
According to court documents, Judge Phyllis Hamilton granted WhatsApp's motion for summary judgment, determining that NSO Group violated the Computer Fraud and Abuse Act (CFAA), the California Comprehensive Computer Data Access and Fraud Act (CDAFA), and breached WhatsApp's terms of service.
The case stems from a 2019 incident where NSO Group allegedly used WhatsApp's system to send malware to approximately 1,400 mobile devices. The court found that NSO Group's WhatsApp Installation Server (WIS) sent messages through WhatsApp's California-based servers 43 times during May 2019 to deploy the Pegasus spyware.
The technical details of the case reveal that NSO Group created a modified version of the WhatsApp application that allowed its clients to send "cipher" files with "installation vectors." These files enabled the surveillance of target users by extracting information from their devices.
During the litigation, NSO Group faced sanctions for failing to produce Pegasus source code in a usable manner. The company made the code viewable only by Israeli citizens while in Israel, which the court deemed "impracticable for a lawsuit that is to be litigated in this district."
The court rejected NSO Group's argument that they lacked responsibility because their government clients operated Pegasus. Judge Hamilton determined that NSO Group's intentional redesign of Pegasus to evade detection after WhatsApp fixed the security breach demonstrated clear intent to violate computer access laws.
The ruling marks a significant development in the regulation of commercial spyware. NSO Group had previously attempted to claim immunity from such lawsuits, arguing that their software was used by government clients for national security purposes.
Senior Researcher John Scott-Railton at Citizen Lab characterized the ruling as a "big win for spyware victims" and a "big loss for NSO." According to court documents, a jury trial scheduled for March 3, 2025, will determine the damages NSO Group must pay to WhatsApp.
BREAKING: NSO Group liable for #Pegasus hacking of @WhatsApp users.
— John Scott-Railton (@jsrailton) December 21, 2024
Big win for spyware victims.
Big loss for NSO.
Bad time to be a spyware company.
Landmark case. Huge implications. 1/ 🧵 pic.twitter.com/hLvEipf6np
The case highlights growing legal scrutiny of the commercial spyware industry. The court found that NSO Group's software obtained protected information by sending data from target users through WhatsApp's servers back to NSO's systems.
Legal experts note this ruling's importance as it establishes precedent for holding spyware companies liable under U.S. computer fraud laws. The decision comes amid increasing international concern about the use of commercial surveillance technology against journalists, activists, and other civilians.
A technical analysis of the case reveals that NSO Group's WIS system performed sophisticated "fingerprinting" of target devices, gathering information about operating systems and memory structures through WhatsApp's servers - capabilities beyond those available to regular WhatsApp users.
The court's decision addresses multiple claims by NSO Group, including jurisdictional challenges and arguments about server targeting. Judge Hamilton concluded that NSO Group's failure to produce complete source code warranted sanctions and supported findings about intentional targeting of California-based servers.
According to Natalia Krapiva, Senior Tech-Legal Counsel at Access Now, the ruling validates experiences of Pegasus victims and promises to impact other cases against spyware companies. The decision establishes that spyware companies cannot evade liability by claiming their government clients bear sole responsibility for surveillance activities.
The court just handed @WhatsApp a major win in the case against NSO Group ⚖️🎉
— Natalia Krapiva 👩🏻💻🕊 (@natynettle) December 21, 2024
NSO was found liable under federal #CFAA & state law for #Pegasus hacking through WhatsApp's servers.
As a lawyer working on surveillance, let me break down the ruling🧵 1/ pic.twitter.com/bCylTmLPEy
The judgment leaves only the question of damages to be determined at trial. Court documents indicate that WhatsApp incurred costs investigating and remediating NSO Group's breaches of their systems.

