Chrome enforces secure connections by default in October 2026
Chrome 154 will enable "Always Use Secure Connections" by default in October 2026, warning users before accessing public sites without HTTPS encryption.
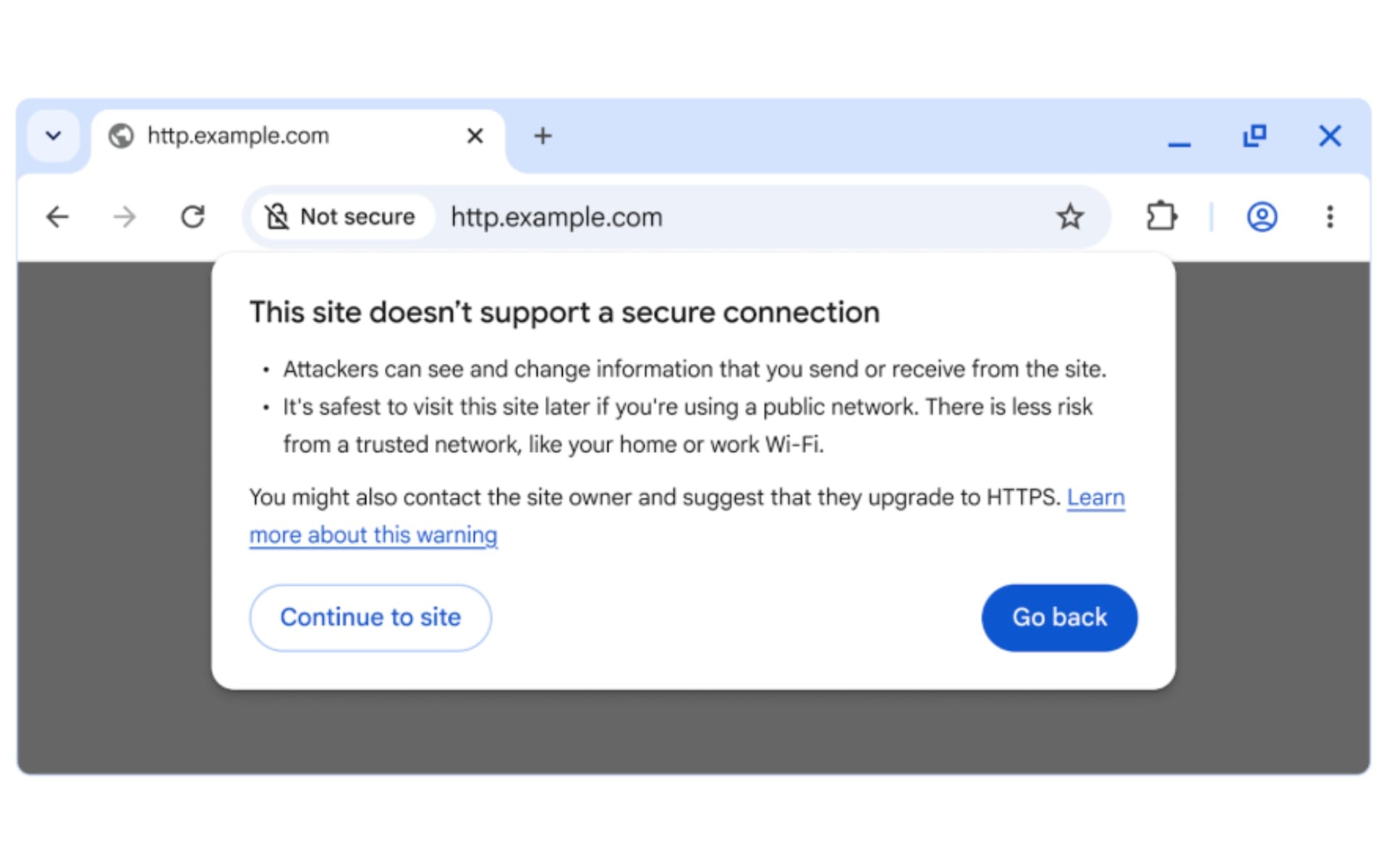
Chrome will ask users for permission before accessing public websites without HTTPS encryption starting in October 2026, according to an announcement published on October 28, 2025. The browser will enable the "Always Use Secure Connections" setting by default with the release of Chrome 154, marking a significant shift in how the browser handles insecure HTTP connections.
The announcement from the Chrome Security Team states that "Chrome will ask for the user's permission before the first access to any public site without HTTPS." This change affects all public websites that have not yet migrated to HTTPS, though private sites like local IP addresses and internal networks will initially be excluded from these warnings.
According to the Chrome Security Team, between 1% and 5% of web traffic may be impacted by this change. The percentage varies significantly across platforms, with Windows showing approximately 95% HTTPS adoption for public sites, while Linux demonstrates nearly 97% HTTPS usage when limiting analysis to public domains only.
Subscribe PPC Land newsletter ✉️ for similar stories like this one
Understanding the security risk
The security team explained that insecure HTTP connections create opportunities for attackers to hijack navigation and force users to load arbitrary, attacker-controlled resources. "When links don't use HTTPS, an attacker can hijack the navigation and force Chrome users to load arbitrary, attacker-controlled resources, and expose the user to malware, targeted exploitation, or social engineering attacks," the announcement stated.
Software designed to hijack navigations is readily available, the team noted. Attackers have previously used insecure HTTP to compromise user devices in targeted attacks. Since attackers only need a single insecure navigation, the widespread adoption of HTTPS by many sites does not eliminate the risk. Any single HTTP navigation may offer a foothold for exploitation.
Many plaintext HTTP connections today are entirely invisible to users. HTTP sites may immediately redirect to HTTPS sites, giving users no opportunity to see Chrome's "Not Secure" URL bar warnings after the risk has occurred. This invisibility prevents users from keeping themselves safe in the first place.
The plateau in HTTPS adoption
For more than a decade, Chrome has published the HTTPS transparency report, which tracks the percentage of navigations in Chrome that use HTTPS. The data shows impressive growth in the report's first several years, starting at around 30-45% in 2015 and reaching the 95-99% range around 2020. Since then, progress has largely plateaued.
The rise represents a tremendous improvement to the security of the web and demonstrates that HTTPS is now mature and widespread. This level of adoption makes it possible to consider stronger mitigations against the remaining insecure HTTP traffic.
While 95% HTTPS adoption might seem to indicate the problem is mostly solved, a few percentage points of HTTP navigations still represents a significant volume of connections. Since HTTP navigations remain a regular occurrence for most Chrome users, a naive approach to warning on all HTTP navigations would be quite disruptive.
Balancing warnings with usability
Chrome has implemented measures to ensure warnings do not become excessive. In all variants of the "Always Use Secure Connections" settings, so long as users regularly visit an insecure site, Chrome will not warn them about that site repeatedly. This means that rather than warn users about 1 out of 50 navigations, Chrome will only warn users when they visit a new or not recently visited site without using HTTPS.
The largest contributor to insecure HTTP traffic, particularly the variation across platforms, is navigations to private sites. Private sites include local IP addresses like 192.168.0.1, single-label hostnames, and shortlinks like intranet. While acquiring an HTTPS certificate trusted by Chrome for a public site is free and easy, obtaining one for a private site remains complicated.
Private names are "non-unique," meaning they can refer to different hosts on different networks. There is no single owner of 192.168.0.1 for a certification authority to validate and issue a certificate to. HTTP navigations to private sites can still be risky, but are typically less dangerous than their public site counterparts because there are fewer ways for attackers to exploit these connections. HTTP on private sites can only be abused by an attacker also on the local network, like on home WiFi or in a corporate network.
When limiting analysis to public sites only, Linux jumps from 84% HTTPS to nearly 97% HTTPS. Windows increases from 95% to 98% HTTPS, and both Android and Mac increase to over 99% HTTPS. In recognition of the reduced risk HTTP to private sites represents, Chrome introduced a variant of "Always Use Secure Connections" for public sites only in 2024.
For users who frequently access private sites, such as those in enterprise settings or web developers, excluding warnings on private sites significantly reduces the volume of warnings those users will see. Simultaneously, for users who do not access private sites frequently, this mode introduces only a small reduction in protection.
Buy ads on PPC Land. PPC Land has standard and native ad formats via major DSPs and ad platforms like Google Ads. Via an auction CPM, you can reach industry professionals.
Experimental validation
In Chrome 141, the browser team experimented with enabling "Always Use Secure Connections" for public sites by default for a small percentage of users. The goal was to validate expectations that this setting keeps users safer without burdening them with excessive warnings.
Analyzing data from the experiment confirmed that the number of warnings seen by users is considerably lower than 3% of navigations. The median user sees fewer than one warning per week, and the ninety-fifth percentile user sees fewer than three warnings per week.
Once "Always Use Secure Connections" becomes the default and additional sites migrate away from HTTP, the actual warning volume is expected to be even lower. In parallel to the experiments, the Chrome team reached out to numerous companies responsible for the most HTTP navigations. Many of these organizations are expected to migrate away from HTTP before the change in Chrome 154.
For many organizations, transitioning to HTTPS is not disproportionately hard but simply has not received attention. Many of these sites use HTTP only for navigations that immediately redirect to HTTPS sites—an insecure interaction previously completely invisible to users.
Implications for local network access
Another current use case for HTTP involves avoiding mixed content blocking when accessing devices on the local network. Private addresses often lack trusted HTTPS certificates due to the difficulties of validating ownership of a non-unique name. This means most local network traffic operates over HTTP and cannot be initiated from an HTTPS page—the HTTP traffic counts as insecure mixed content and is blocked.
One common use case for accessing the local network involves configuring a local network device. A manufacturer might host a configuration portal at config.example.com, which then sends requests to a local device to configure it. Previously, these types of pages needed to be hosted without HTTPS to avoid mixed content blocking.
Chrome recently introduced a local network access permission, which both prevents sites from accessing the user's local network without consent and allows an HTTPS site to bypass mixed content checks for the local network once permission has been granted. This can unblock migrating these domains to HTTPS.
Implementation timeline
The Chrome team will enable the "Always Use Secure Connections" setting in its public-sites variant by default in October 2026 with the release of Chrome 154. Prior to enabling it by default for all users, in Chrome 147, releasing in April 2026, the team will enable "Always Use Secure Connections" in its public-sites variant for the over 1 billion users who have opted into Enhanced Safe Browsing protections in Chrome.
While the transition is expected to be relatively painless for most users, users will still be able to disable the warnings by disabling the "Always Use Secure Connections" setting.
For website developers and IT professionals with users who may be impacted by this feature, the Chrome team very strongly recommends enabling the "Always Use Secure Connections" setting today to help identify sites that may need to be migrated. IT professionals may find it useful to read the additional resources provided to better understand the circumstances where warnings will be shown, how to mitigate them, and how organizations that manage Chrome clients can ensure Chrome shows the right warnings to meet those organizations' needs.
Why HTTPS matters for the web
According to web.dev documentation, HTTPS helps prevent intruders from tampering with communication between sites and users' browsers. Intruders include both intentionally malicious attackers and legitimate but intrusive companies, such as ISPs that inject ads into pages.
Intruders exploit unprotected communications to trick users into giving up sensitive information or installing malware, or to insert their own resources. Intruders exploit every unprotected resource that travels between websites and users. Images, cookies, scripts, and HTML are all exploitable. Intrusions can occur at any point in the network, including a user's machine, a WiFi hotspot, or a compromised ISP.
HTTPS prevents intruders from passively listening to communications between websites and users. One common misconception about HTTPS is that only websites handling sensitive communications need HTTPS. Every unprotected HTTP request can potentially reveal information about users' behaviors and identities.
A single visit to one unprotected website might seem benign, but some intruders look at users' aggregate browsing activities to make inferences about their behaviors and intentions, and to de-anonymize their identities. Employees might inadvertently disclose sensitive health conditions to their employers just by reading unprotected medical articles.
Powerful new web platform features, such as taking pictures or recording audio with getUserMedia(), enabling offline app experiences with service workers, or building progressive web apps, require explicit permission from the user through HTTPS. Many older APIs are also being updated to require permission to execute, such as the Geolocation API. HTTPS is a key component of the permission workflows for both new and updated features.
Impact on digital marketing
The change represents the latest development in Chrome's ongoing security initiatives. For marketers and website owners, ensuring all web properties use HTTPS encryption becomes critical to maintaining user access without friction.
The marketing community has tracked Chrome's security features closely. Browser security measures affect user experience, conversion rates, and website traffic. Sites that have not yet implemented HTTPS encryption face potential disruption when users encounter security warnings starting in April 2026 for Enhanced Safe Browsing users and October 2026 for all Chrome users.
The requirement creates particular challenges for advertisers running campaigns to landing pages without HTTPS. Users may abandon sessions when presented with security warnings, directly impacting campaign performance and return on ad spend. IT departments and development teams should prioritize HTTPS migration projects before the April 2026 rollout begins.
Enterprise environments with internal tools and applications hosted on private networks receive an exemption from the initial warnings. However, organizations should evaluate long-term strategies for implementing HTTPS across all properties, including internal systems, to maintain consistent security standards.
Looking forward
While warning on insecure public sites represents a significant step forward for web security, additional work remains. The Chrome team hopes to work to further reduce barriers to adoption of HTTPS, especially for local network sites. This work will hopefully enable even more robust HTTP protections in the future.
The announcement follows a pattern of increasing security requirements across major browsers. As other platform security measures continue to reshape the digital landscape, website operators must adapt to evolving technical requirements. The shift to HTTPS by default marks another milestone in this ongoing transformation.
Website operators can prepare by auditing their properties for HTTP connections, implementing HTTPS certificates, and testing the "Always Use Secure Connections" setting in Chrome today. Organizations managing Chrome deployments can review policy options to ensure the setting aligns with their security requirements while minimizing user disruption.
Subscribe PPC Land newsletter ✉️ for similar stories like this one
Timeline
- 2015: HTTPS adoption in Chrome ranges from 30-45% of navigations
- 2020: HTTPS adoption reaches 95-99% range, with growth beginning to plateau
- 2022: Chrome launches "Always Use Secure Connections" as opt-in option
- October 28, 2025: Chrome Security Team announces plans to enable "Always Use Secure Connections" by default
- April 2026: Chrome 147 enables "Always Use Secure Connections" for Enhanced Safe Browsing users (over 1 billion users)
- October 2026: Chrome 154 enables "Always Use Secure Connections" by default for all users
Subscribe PPC Land newsletter ✉️ for similar stories like this one
Summary
Who: The Chrome Security Team at Google, specifically Chris Thompson, Mustafa Emre Acer, Serena Chen, Joe DeBlasio, Emily Stark and David Adrian, announced the change. The decision affects all Chrome users globally, website developers, IT professionals, and organizations managing Chrome deployments.
What: Chrome will enable the "Always Use Secure Connections" setting by default starting in October 2026 with Chrome 154. The browser will ask users for permission before accessing any public site without HTTPS encryption. The setting will show a bypassable warning when HTTPS is unavailable. Private sites, including local IP addresses and internal networks, are excluded from the initial implementation.
When: The announcement was published on October 28, 2025. The phased rollout begins in April 2026 with Chrome 147 for Enhanced Safe Browsing users, then extends to all users in October 2026 with Chrome 154. Experimental testing began in Chrome 141.
Where: The change affects Chrome browser users worldwide across all platforms including Windows, Mac, Linux, and Android. The impact varies by platform, with current HTTPS adoption ranging from 84% on Linux to over 99% on Android and Mac for public sites. Private network sites receive an exemption from the warnings.
Why: The Chrome Security Team aims to protect users from attackers who exploit insecure HTTP connections to hijack navigation, install malware, or conduct social engineering attacks. Despite HTTPS adoption reaching 95-99% overall, the remaining HTTP traffic creates persistent security risks. Many HTTP connections are invisible to users, providing no opportunity to recognize or avoid the danger. The change balances user safety with usability by warning only on new or infrequently visited insecure sites while excluding private networks where HTTPS implementation faces technical barriers.

